In today’s information age, mobile apps have become a prevalent means of processing a significant amount of personal and payment-related data. In the event that these apps are vulnerable, malicious actors may exploit security gaps to obtain sensitive information for their own gain. Thus, ensuring app security is crucial in safeguarding data transmitted over the internet through mobile apps. I would like to introduce a tool called OWASP ZAP, that simplifies the analysis of app security and provides actionable recommendations for improving it. Let’s see how to Identify mobile app vulnerability.
How OWASP ZAP Tool can help
ZAP Tool is a proxy tool that intercepts network connections to analyze data for known vulnerabilities. By doing so, it assists in identifying security issues. This software is designed to be used as a security testing tool for applications and is capable of automatically scanning applications to identify vulnerabilities. ZAP is an open-source project developed by the Open Web Application Security Project (OWASP), a non-profit organization dedicated to improving software security. Its user-friendly interface and automated features make it a popular choice for security professionals seeking to identify and remediate vulnerabilities in mobile apps and web applications.
Let’s look at how to set up the ZAP tool and identify the mobile app vulnerability.
How to set up the ZAP tool
To utilize the ZAP tool, download it through the provided link and proceed to install it. Next, generate the SSL root certificate for the ZAP proxy by navigating to the “Tools” menu, selecting “Options,” and then choosing “Dynamic SSL Certificates.” Click the “Generate” button to create a new certificate, and save it in a preferred location. Finally, install the certificate on the test device by transferring it via email, which is the simplest method. Following these steps will allow the ZAP tool to intercept and analyze network traffic, and enable efficient identification of potential security issues in the tested mobile app.
To activate the tool for use, proceed to set up the proxy by accessing the “Tools” menu, selecting “Options,” and then navigating to “Local Proxies.” In the “Address” field, input “0.0.0.0” to bypass all network calls, and in the “Port” field, input “8080.” Once these settings have been properly configured, the ZAP tool is now fully operational and ready for use. Its proxy functionality can effectively intercept and analyze network traffic, allowing us to identify mobile app vulnerability.
Let’s set up the device
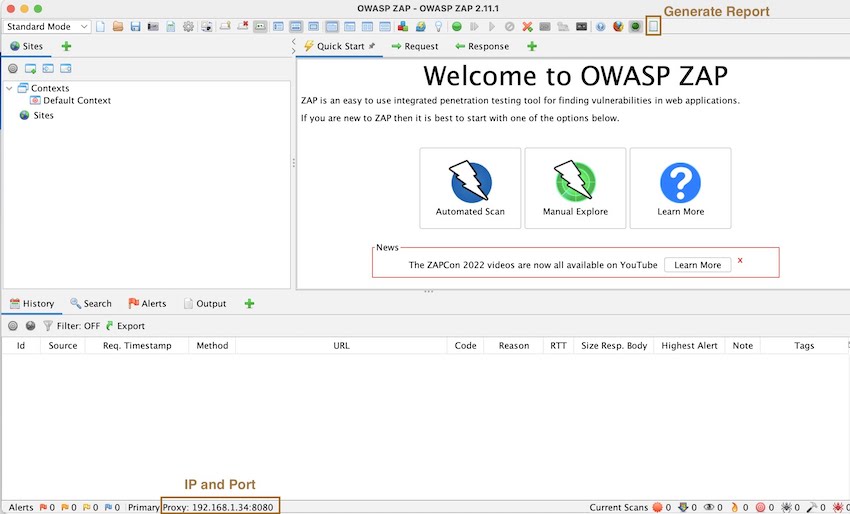
To configure the device for the proxy tool, begin by locating the IP address as indicated at the bottom of the screenshot. Next, navigate to the Wi-Fi settings on the device, and input the previously located IP address and port number as shown in the screenshot. With these settings in place, the device is now properly configured to function with the proxy tool. The tool can now effectively intercept and analyze network traffic, allowing for the identification and helping us to Identify mobile app vulnerability.
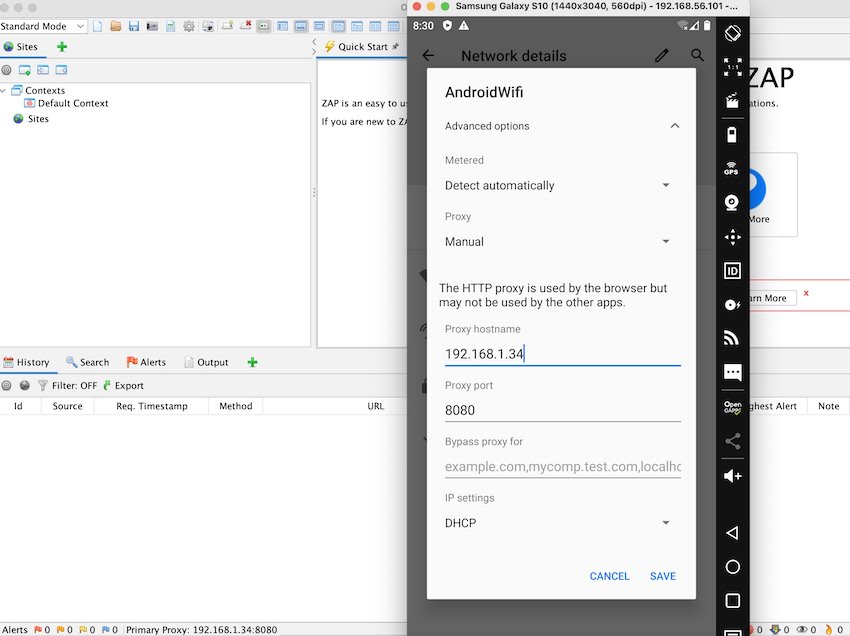
Time to generate the report for the mobile app!
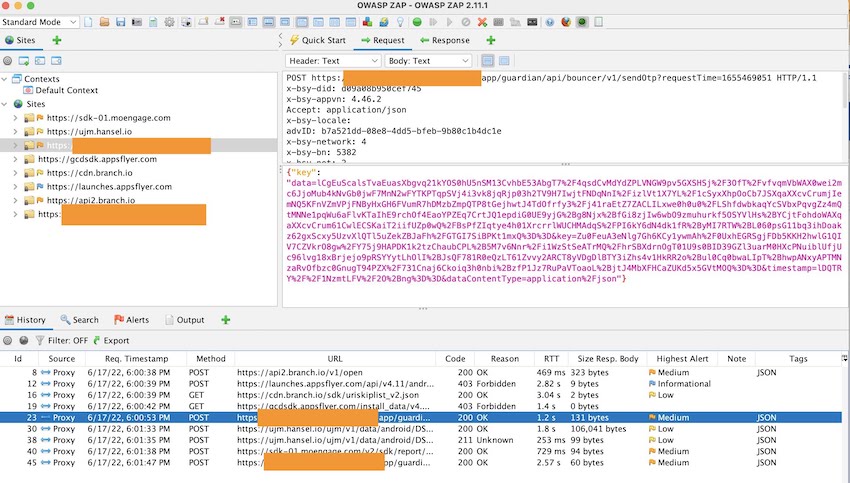
As an example, we will utilize a sample app. First, install the app on the test device, and perform all necessary app functions to capture network logs using the ZAP tool. All network calls can be accessed through the History section of the ZAP tool. You may wonder how the SSL pinned app can be intercepted, Stay tuned for an easy method to bypass the SSL pinning. After completing the required app functions, generate a report by selecting the “Generate Report” option as illustrated in the provided screenshot. This report can be used to identify mobile app vulnerability, with the most common security issues being easily identified.
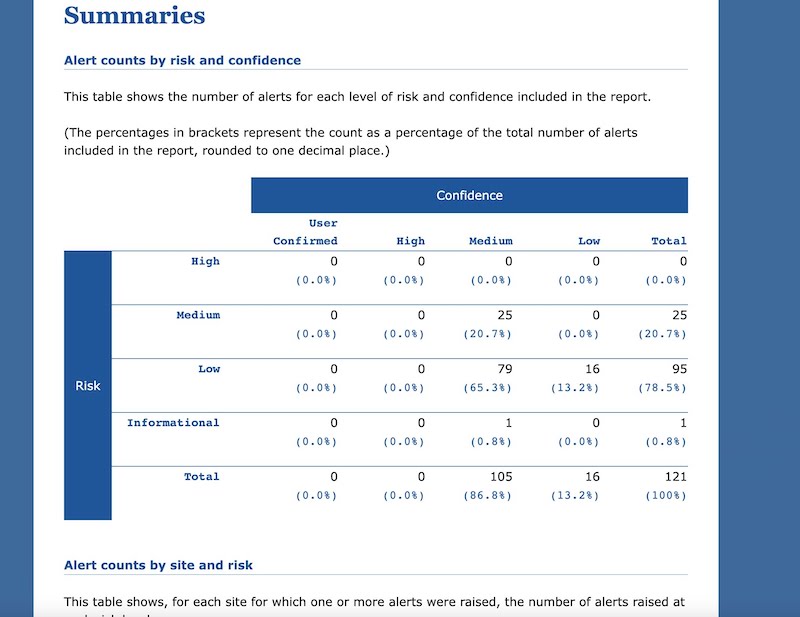
Conclusion
I hope this article helped you to configure the test device and set up the ZAP tool to identify mobile app vulnerability in a short period of time. You can use the same steps in both iOS and Android devices to identify mobile app vulnerability.
Written By

I’m an Enterprise Architect at Akamai Technologies with over 14 years of experience in mobile app development across iOS, Android, Flutter, and cross-platform frameworks. I’ve built and launched 45+ apps on the App Store and Play Store, working with technologies like AR/VR, OTT, and IoT.
My core strengths include solution architecture, backend integration, cloud computing, CDN, CI/CD, and mobile security, including Frida-based pentesting and vulnerability analysis.
In the AI/ML space, I’ve worked on recommendation systems, NLP, LLM fine-tuning, and RAG-based applications. I’m currently focused on Agentic AI frameworks like LangGraph, LangChain, MCP and multi-agent LLMs to automate tasks